7 API Security Best Practices to Maintain Application Security

Author : TechAffinity 2nd Feb 2023

With the growing demand to build applications and the unprecedented rise in microservices architecture, Application Programming Interfaces (APIs) have become an integral part of application development. On the one hand, APIs have made it easier for third-party developers to integrate with apps and helped customers benefit from the integrations. However, it is a challenge to maintain app security with the increasing number of smaller parts in apps that communicate with each other.
Some of the most significant security breaches in recent memory have involved API breaches. For example, a Facebook API loophole led to the Cambridge Analytica scandal, exposing the personal information of more than 50 million users. Similarly, businesses like Venmo, USPS, and British Airways have also suffered setbacks.
Hence, there is an urgent need to employ the best API Security practices to enjoy the benefits that APIs offer while keeping your data safe.
The Need for API Security
APIs are the doorways to the highly-sensitive and confidential data of your organization. They provide the means for two applications to communicate with each other. APIs are the core component of the microservices architecture and help developers build client-side applications which deal directly with the consumers. The client-side interacts with the server side of an application through the API. Since APIs are available on public networks and well documented, they can be reverse-engineered and are prone to cyber-attacks.
According to the 2022 API Security Trends Report, the API usage trends have revealed that more than 41% of the organizations involved in the study had an API security incident reported in the last 12 months. 63% of these incidents involved data breaches or data loss. API problems include poor API logging practices, API authentication problems, and API misconfigurations.
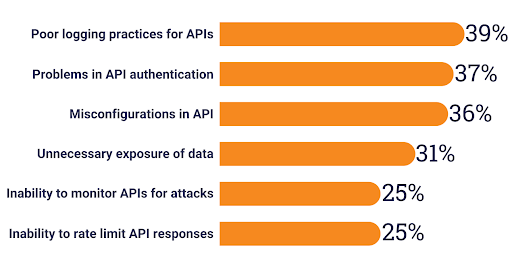
More than a third (35%) of the survey respondents suggested that the project delays were due to API security issues. 87% of the respondents reported that more effective integration of API security testing could prevent these delays. About a fourth (25%) of the respondents felt the inability to monitor the APIs from attacks led to project delays.
Types of API CyberAttacks
The primary goal of an API is to ensure the secure transfer of private data between the application and external users. Hence, a poorly configured API can result in unauthorized access to sensitive data.

1. Stolen Authentication
One of the widely used methods of gaining access to an API is impersonating the identity of an authorized user. An authentication token in the wrong hands can compromise your resources as the hacker gains unauthorized access while seeming genuine. Furthermore, they can steal sensitive information by trying to guess the authentication passwords or by breaking a weak authentication process.
2. Man-in-the-Middle Attack
When a hacker attempts to intercept an API request or response between the user and the API and succeeds, it results in a man-in-the-middle (MITM) attack. It leads to the exposure of sensitive data like account login credentials or manipulating the contents of the API data.
3. Code Injections
Whenever APIs have gaps in their validation requests and authentication tokens, there is scope for code injections, which may result in hackers inserting a script into your application server through an API request. This script intends to plant false information, steal or delete data, and cause adverse effects on your internal mechanism. For example, hackers target SQL databases with SQL injections.
4. Denial-of-Service Attack
Denial-of-service (DoS) attacks inundate your application server with API requests so that it slows down, breaks, or ultimately crashes. Since most of these attacks originate from multiple sources simultaneously, they are known as distributed denial-of-service (DDoS) attacks.
Though APIs involve such risks, they are here to stay. Therefore, software integration is needed to ensure the best API security measures.
API Security Best Practices
You can protect APIs from malicious attacks and unauthorized access with API Security best practices. You can do this by ensuring all the requests to the API are from trusted sources. You also have to validate all the API requests and encrypt all the responses given by the API. By leveraging the following API Security best practices, you can significantly reduce the risks associated with any API.
1. Identify API Risks & Vulnerabilities
To be resilient to cyber-attacks, you must be able to identify the parts of your API that are prone to security vulnerabilities and risks. You need to identify which data and what part of the system is most vulnerable to attacks and adopt an appropriate recovery plan to lower the risks. To address these vulnerabilities, you ought to discover them in the initial phases of development.
For large organizations that use thousands of APIs at the same time, this might be challenging. For such scenarios, you can use API security testing. You can check the OWASP Top 10 Securities Vulnerabilities list to reduce the biggest API threats.
2. Enforce Authorization & Authentication
Together, authorization and authentication can be powerful tools to combat cyberattacks. You can use authentication to verify the user’s identity. You can determine the user access permissions using authorization.
You can do API authentication using a password, multi-factor authentication, or tokens, which securely verify the user’s identity. To authenticate the request, API matches the authentication tokens with the ones in the database, helping you to keep track of trusted sources using your resources. OAuth is one of the widely accepted protocols for API authentication.
API authorization starts after the identity of the user is confirmed using authentication. It involves verifying if the users or the applications have the required permissions to access the API. You can define authorization by user roles, with each user role having different access permission. For example, a user might have access to the resources without being able to add any new information. In the case of APIs, you should operate under the principle of least privilege, which states that users must have access only to the necessary resources and methods.
3. Validate All Requests & Encrypt Data
Sometimes hackers might try to gain access to your application while appearing genuine. So, you ought to validate every possible incoming request through a well-defined validation process before it reaches the data layer. Hence, you eliminate any harmful code or script at the processing stage.
Data encryption is mandatory in securing data, especially personal information such as passwords or payment information. You can encrypt all the data using widely accepted protocols such as Transport Layer Security (TLS) or Secure Sockets Layer (SSL).
4. Expose Only the Necessary Information
When thinking about API security, it is often easy to think about only blocking malicious information while ignoring the threat of exposure to confidential information. Since APIs include sensitive information like passwords and keys, you should share only the relevant information with the end user. For example, in an API response, you should include only the status of the request, like success or failure, and any other information directly related to the resource.
5. Implement API Rate Limiting
One commonly used method to attack an API is to flood it with several requests. It overwhelms the API and results in performance degradation and availability issues. As the popularity of APIs increases, such DDoS attacks are bound to happen regularly. You can rate-limit the API requests in two ways, Quotas, and Throttling. Quotas limit the number of requests that can be made to the API by a user over a given duration, while Throttling slows down the connection while allowing the user to use the API. Thus, you can prevent floods of traffic or unexpected sudden spikes in API requests.
6. Monitor & Log API Activity
You can enforce API security by maintaining a log history for troubleshooting errors. It helps you to audit and log the relevant information on the production server. In case of a hack, keeping an active log history can help trace the source of the incident to remedy the error. It also functions as a resource for debugging, tracking, and monitoring any suspicious activity within the application. By logging all API activities, developers can reverse engineer any attack and take adequate measures to prevent similar incidents in the future.
7. Establish API Firewalls
To prevent immigration issues, you can establish API firewalls. You can implement this in two layers:
- DMZ layer – The first layer of security, which works with the API firewall and executes simple security measures for early detection and blocking of intruders. It includes checking the message size, SQL injections, and any security in the HTTP layer.
- LAN – The second layer of security performs advanced security mechanisms on the content.
Final Thoughts
As organizations migrate from monolithic to microservices architecture, the use of APIs continues to grow exponentially, and with it comes the need for enhanced security. It is time to stop taking API Security for granted. A lapse in security exposes your user information and undermines trust in your organization. While there is no doubt that API offers a lot of exciting possibilities, without the proper security measures, you stand to lose your credibility and reputation. You should ensure API Security by combining the right technology with a streamlined approach and building security into the design process to rectify issues as soon as possible.
For further information on data security, please send your queries to media@techaffinity.com or get in touch by scheduling a meeting with our developers.