Common Web Security Vulnerabilities and 4 Ways to Avoid Them

Author : TechAffinity 9th Aug 2022

Even the most experienced CIO and web security expert must stay vigilant and guard against the bad guys. No one is safe without knowing what to look out for. It has always been a matter of concern that any web app might have some security vulnerabilities that can result in security loopholes. The need of the hour is for businesses to start paying attention and take the following measures to avoid common web security vulnerabilities. Web security vulnerabilities are prioritized depending on exploitability, detectability, and impact on software.
1. No Random Code
One of the easiest ways that you can be misled is by replicating and copy-pasting random code from repositories like Github and Bitbucket. You would be better off if you assume that No Random code is Safe code.

It is important to verify the authenticity of the source before copy-pasting any code. It is a good practice to test every piece of code for possible Malware. Remember, Prevention is better than cure. So, do the needed precautions and resist the temptation to simply copy-paste code from the internet.
Normally, you have the maintenance mode. You could initially check the code there, work on possible improvements, make adjustments and optimizations on the code, and then further subject it to final tests. This code can be put under some rounds of rigorous testing security to ensure it meets the necessary standards. Once you are sure of all the changes, you can take it to the production environment and commit the final changes.
For eg, Vulnerable WordPress plugins when exposed to such scams can end up damaging your website. One of the major issues is that these plugins can get backdoor access to the websites and gain administrative access. Now, using this backdoor entry, they can take over a website, remove its index from Google, and make it appear non-existent in the SERP.
2. Encrypt Sensitive Information
To keep data safe and secure, encryption is crucial. When it comes to sensitive data, you cannot take anything for granted and security needs to be the top priority at all times. According to the NSA( National Security Agency), one of the safest options to use is to go for the AES(Advanced Encryption Standard) encryption model. Even the US government classified documents use this encryption.
AES-256 is the best of the lot with other ciphers like AES-192 and AES-128, also very capable of providing you with strong encryption methods. Each cipher does the encryption and decryption in 128-bit blocks and ensures elevated security every step of the way.
For those running an eCommerce store, for integrating and accepting payment options, you need to secure your website with a TLS certificate and user data should always be shared over a secure connection. Without a secure connection, it becomes that much easier for the hacker to siphon off precious data from the card during the transaction.
3. PCI-Compliant Encrypted Payment Systems
Companies big and small are feeling the effects of the rapid pace of transformation and the coming years are clearly about making fundamental shifts in how you operate and manage your business.
When it comes to online payments and transactions, being PCI-compliant (Payment Card Industry) is one such fundamental prerequisite. At times, when you accept credit card information for recurring billing, they might get compromised.

The primary issue with storing credit card information is that you become a focused target for hackers. Your servers are now targeted by these hackers around the world and both your credit and debit card information is at risk.
You need someone who is PCI-savvy because it needs to be updated at regular intervals of time and the information also needs to stay updated with the latest trends and technologies. This is why PCI-compliant systems can get difficult.
There are other options like using a payment processor that can do significant work for you and help you save on installation, support, and maintenance costs. While storing credit card information, especially ensure that the files that store the information and the hardware where they are stored are both encrypted for web security.
4. Adequate User Authentication Controls
Authentication-related web security vulnerabilities can be majorly attributed to the improper implementation of proper user authentication controls. This may result in user accounts being compromised or in the case of big companies several millions of user accounts being compromised. Now hackers end up having complete control over the user accounts of people and this results in massive privacy and web security issues.
There are usually three ways hackers can exploit a defective system. The first method is the Credential Stuffing, the second one is the Brute-force method, and the final method is Session Hijacking.
In Credential Stuffing, the attackers will continue trying different sets of usernames and passwords acquired from another attack and use it, till they find a genuine combination of username and password.
In Brute-force, every single character combination that is possible is tried until the hacker breaks into the system.
In Session Hijacking, due to a failure to invalidate session IDs properly, the hackers sneak into the system and take control of the session of a valid user.
You can handle this web security vulnerability by making sure that there is enough time for the developer to test the code before it gets deployed. Also, implementing multi-factor authentication is an important security feature that can be considered. If possible, avoid restricting the input size of passwords since as characters increase guessing the right combination also becomes really difficult. To prevent brute force, you can use some form of lockout mechanism.
What are Web Security Vulnerabilities?
A website vulnerability is a flaw/bug in the software code, a system misconfiguration, or another weakness in the web application or its components and processes. Web application security vulnerabilities allow attackers to get unauthorized access to the organization’s systems, processes, and mission-critical assets. With such access, attackers can orchestrate attacks, take over applications, use privilege escalation to steal data, disrupt large-scale services, and so on.

The OWASP Top 10 Web Security Vulnerabilities
The OWASP (Open Web Application Security Project) Top 10 is a standard awareness document for web application security and developers. It reflects widespread agreement on the most security threats to web applications. Using the OWASP Top 10 is likely the most effective first step toward changing your organization’s software development culture to one that produces more secure code.
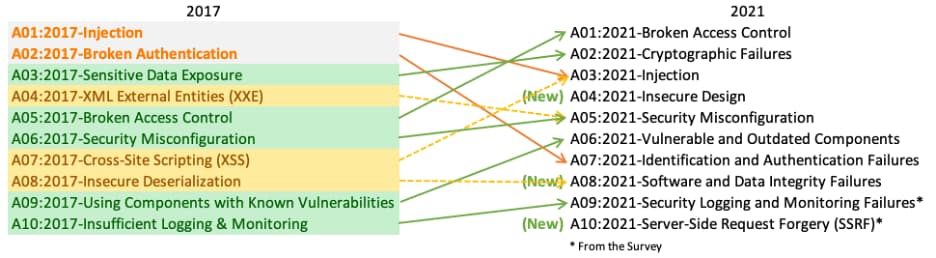
1. Broken Access Control
Access control ensures that users stay inside the bounds of their specified permissions. Failures frequently result in unauthorized information leaks, alteration or deletion of all data, or the execution of business operations outside the user’s limits.
2.Cryptographic Failures
The requirements for data protection both in transit and at rest will be the first step. Passcodes, credit card details, medical histories, personal info, and trade secrets, for instance, need extra security, especially if they are covered by privacy laws like the EU’s General Data Protection Regulation (GDPR) or rules like the PCI Data Security Standard, which protects financial data (PCI DSS)
3. Injection
An injection vulnerability is a weakness that enables a hacker to send malicious files through an application to another system. To do this, it may be necessary to compromise the vulnerable application’s backend systems and also other clients attached to them.
4. Insecure Design Attack
The term “missing or ineffective control design” refers to a broad category of flaws called “insecure design.” All other Top 10 risk categories are also not inferred from insecure design. Insecure implementation differs from insecure design. We distinguish between implementation defects and design errors for a purpose that have different root causes and corrective actions. Even a secure design can have implementation flaws that create vulnerabilities that can be misused. Because necessary security controls were by definition never developed to defend against specific attacks, an insecure design can be fixed by a flawless implementation.
5. Security Misconfiguration
Security controls that have been incorrectly configured or left unsecured are known as security misconfigurations and put your network and information at risk. Generally, any poorly implemented configuration changes, computer settings, or a technical problem across any component in your endpoints could result in a misconfiguration.
6. Vulnerable and Outdated Components Vulnerability Security
A module, software package, or API is an example of a software component, which is a part of a system or application that increases the functionality of the application. Software components that are unsupported, out of date, or exposed to a known exploit are considered component-based vulnerabilities.
7. Identification and Authentication Failures
A module, software package, or API is an example of a software component, which is a part of a system or application that increases the functionality of the application. Software components that are unsupported, out of date, or exposed to a known exploit are considered component-based vulnerabilities.
8. Identification and Authentication Failures
When a user’s identity, authentication, or session management functions are improperly implemented or inadequately protected by an application, identification and authentication failures may result.
9. Software and Data Integrity Failures
Lack of adequate logging, monitoring, or reporting of security events, such as login attempts, makes it challenging to identify suspicious behavior and significantly increases the likelihood that an attacker will be successful in exploiting your application.
10. Server-Side Request Forgery
When a web application retrieves a remote resource without checking the user-supplied URL, SSRF vulnerabilities can occur. Even when the application is shielded by a firewall, VPN, or another type of network access control list, it enables an attacker to force the application to send a crafted request to an unexpected destination (ACL).
Fetching a URL becomes a typical scenario as a convenient feature for end users offered by modern web applications. Because of this, SSRF is becoming more common. Additionally, cloud services and complex architectures are increasing SSRF severity.
Final Thoughts
When it comes to website security, it is important to be aware of what works for your business and stay updated with the technology needs. The common web security vulnerabilities are much more basic than one might consider. By being informed and prepared, you can keep your business secure and do a much better job of dealing with such vulnerabilities.
At TechAffinity, we know how to avoid web security vulnerabilities and believe that keeping it simple and precise is crucial in getting our business practices right for serving our customers in the best way possible. In case of any business inquiries, shoot them to media@techaffininty.com or schedule a meeting with our experts.